Token Management
Access tokens
Access tokens are issued by the Service Provider's authorization servers. There are no special requirements regarding content and structure of access tokens and the platform does not validate these tokens.
Important information about access tokens:
- Access tokens are treated as black boxes by clients and bLink.
- No changes required at Service Provider's authorization servers.
- Allows use of symmetric token signing algorithms for JWTs.
Authorization code and token lifetime
The following table defines mandatory and recommended lifetimes for authorization code and access/refresh tokens.
| Code/Token | Lifetime | Type | Comment |
|---|---|---|---|
| Authorization code | 30 sec | Mandatory | The authorization code flow consists of a few redirects without user interaction. It is feasible to keep this lifetime short. |
| Access token | 24 hr | Recommendation | Shorter lifetime could lead to token refresh flow for almost every resource access. |
| Refresh token | 30 days | Minimum required lifetime | Refresh token lifetime has to be extended with every access token refresh. |
The access token expiration must be handled by the token issuer (Service Provider).
Tokens stored by bLink (CaaS) will be deleted after three months of inactivity.
Authorization revoke
- see Permission Revocation (in case of Consent Management 2.0 with CaaS)
- see Token Revocation (in case of Consent Management 2.0)
Multiple tokens for the same e-banking contract
Some Service Providers allow only one token per bank contract.
In case that two consent flows with the same provider are performed and the resource owner uses the same contract to log into the e-banking, then the token issued for the first completed consent flow will be revoked by the second. There is no notification that the existing token was revoked and can only be identified by a failing refresh-call.
Service Provider IAM endpoints
The Service Provider must expose the authorization endpoint to the internet. The token endpoint may be exposed solely to bLink, which acts as an authenticating proxy toward the token endpoint and protects it from unauthorized access.
Secure Token Storage
Access and refresh tokens have a sensitive nature and must be protected. They need to be secured according to generally accepted best practices for secure password storage.
Request validation
Only valid requests are forwarded by bLink to Service Providers. Requests from authenticated and authorized clients must meet the following requirements:
- All mandatory request headers are present and syntactically correct
- All optional request headers are syntactically correct
- No unspecified request headers are present
- JSON or XML payload is syntactically correct
Service Providers must validate that the access token in the request was issued (by the authorization server) to the client authenticated by bLink.
Token Refresh without CaaS
The token refresh flow is implemented according to OAuth 2.0 standard.
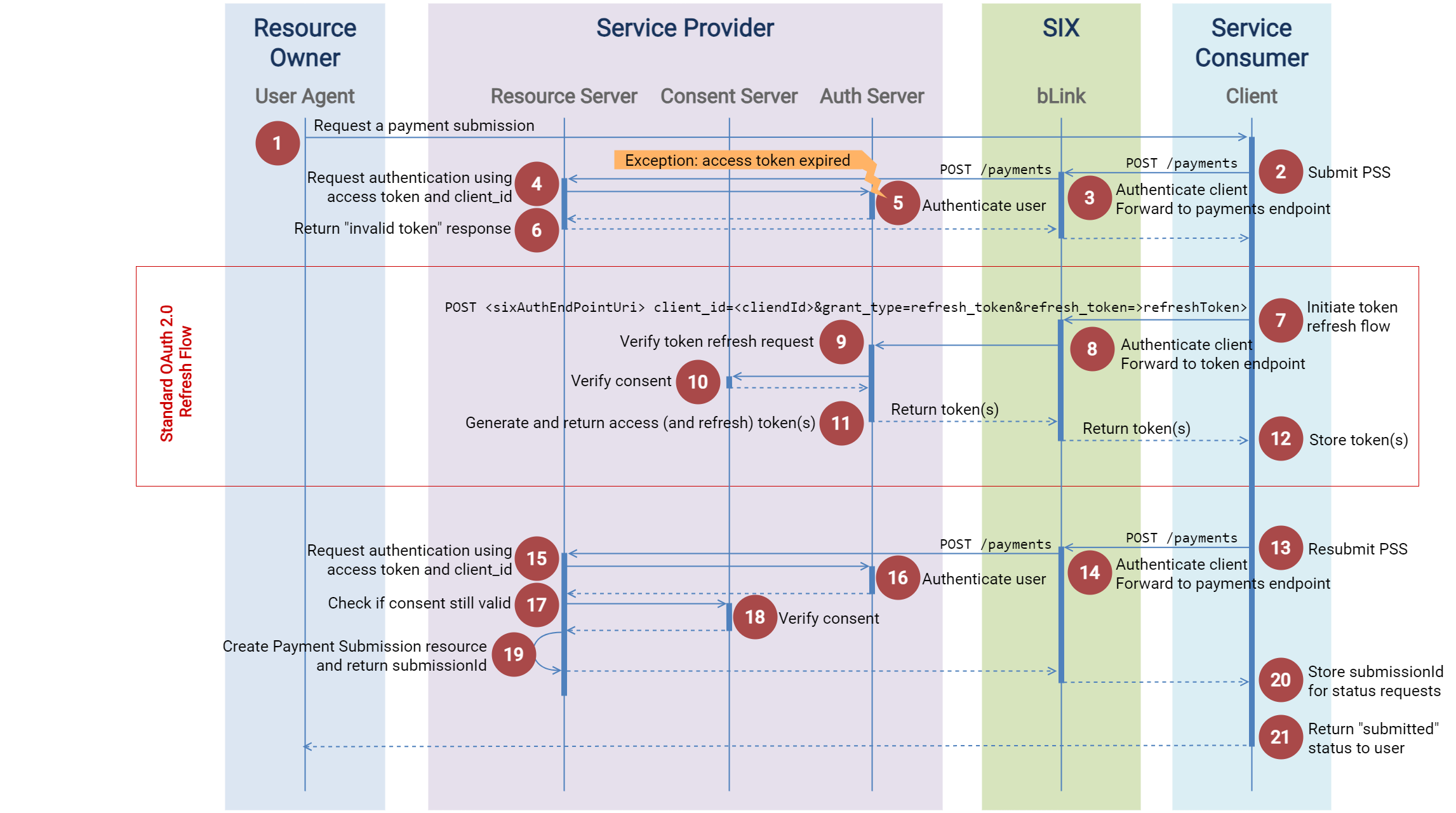
Example of token expiration and subsequent refresh flow
This example shows a payment initiation submission with an expired access token, subsequent token refresh and resubmission of initial payment initiation.
-
Payment service user (PSU) is logged in at a client and submits a payment initiation.
-
Client
- stores IP address and User Agent of PSU
- prepares PSS message
- posts the message to bLink API including
X-PSU-IP-AddressandX-PSU-User-Agentheaders (mandatory for PSS)
Example from client to SIX:
POST /api/bankingservices/b-link-consent-type/payment-submission-service/version/payments
x-corapi-target-id: 99999
host: api.six-group.com
authorization: Bearer ZXlKMGVYQWlPaUpLVjFRaUxDSmhiR2Np
x-psu-ip-address: 34.12.19.3
x-psu-user-agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/47.0.2526.111 Safari/537.36
... -
bLink API payments endpoint
- authenticates the client
- verifies authorization to payments endpoint
- validates the request
- forwards the request to the Service Provider
Example from SIX to Service Provider:
POST /proprietaryBackendPath/payments
x-corapi-client-id: 654321
host: api.fi.example.com
authorization: Bearer ZXlKMGVYQWlPaUpLVjFRaUxDSmhiR2Np
x-psu-ip-address: 34.12.19.3
x-psu-user-agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/47.0.2526.111 Safari/537.36
... -
Resource Server of the SP extracts access token and client_id from PSS request and calls Auth Server to authenticate user.
-
Auth Server detects that access token is expired and returns an "invalid token error".
-
Resource Server takes "invalid token error" and returns it via bLink API to the client. According to RFC6750 Section-3 the response must include the "WWW-Authenticate" response header in this case.
-
Client initiates standard OAuth 2.0 token refresh flow
Example from client to SIX:POST /api/bankingservices/b-link-consent-type/consent-flow/version/oauth/token
x-corapi-target-id: 99999
host: api.six-group.com
client_id: 654321
grant_type: refresh_token
refresh_token: WVhRaU9qRTFOREV4TkRneE1Ea3NJbVY0 -
bLink API token endpoint
- authenticates the client
- extracts the IID from the
X-CorAPITarget-IDrequest header - determines the hostname/IP address and basepath of Auth Server token endpoint at target SP
- sends token request with header
X-CorAPI-Client-IDto target SP
Example from client to SIX:
POST /proprietaryBackendPath/oauth/token
x-corapi-client-id: 654321
host: api.sp.example.com
client_id: 654321
grant_type: refresh_token
refresh_token: WVhRaU9qRTFOREV4TkRneE1Ea3NJbVY0 -
Auth Server token endpoint of Service Provider
- authenticates Client using request header
X-CorAPI-Client-ID - verifies refresh_token (must have been issued to the Client authenticated from the request header)
- calls Consent Server for consent verification
- authenticates Client using request header
-
Consent Server verifies consent
-
Auth Server
- generates a new access token
- and either generates a new refresh token or extends the lifetime of the refresh token
- returns an access token and optionally refresh token via bLink API to the client. If the request fails for any reason, the Auth Server should inform the resource owner according to OAuth 2.0 specification, 5.2.
-
Client stores the new access token (and optionally refresh token).
-
Client resubmits the PSS message from step 2
Example from client to SIX:
POST /api/bankingservices/b-link-consent-type/payment-submission-service/version/payments
x-corapi-target-id: 99999
host: api.six-group.com
authorization: Bearer 9pWlMxaVlXNXJhVzVuTFhWelpYSXRhV1Fp
x-psu-ip-address: 34.12.19.3
x-psu-user-agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/47.0.2526.111 Safari/537.36
...
- bLink API payments endpoint
- authenticates the client
- verifies authorization to payments endpoint
- validates the request
- forwards the request to the Service Provider
Example from SIX to Service Provider:
POST /proprietaryBackendPath/payments
x-corapi-client-id: 654321
host: api.fi.example.com
authorization: Bearer 9pWlMxaVlXNXJhVzVuTFhWelpYSXRhV1Fp
x-psu-ip-address: 34.12.19.3
x-psu-user-agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/47.0.2526.111 Safari/537.36
... - Resource Server of Service Provider extracts access token and client_id from PSS request and calls Auth Server to authenticate user.
- User is authenticated using access token and client_id.
- Resource Server calls Consent Server to verify consent.
- Consent Server verifies / returns consent.
- Resource Server
- stores/forwards
X-PSU-IP-AddressandX-PSU-User-Agentfor fraud detection systems - creates PSS resource
- returns response containing
submissionIdvia bLink API to Client
- stores/forwards
- Client stores
submissionIdfor consecutively polling the status of the PSS request. - Client returns page showing "PSS submitted" status to user.
Token refresh with CaaS
In case of CaaS, the Token handling is completely hidden from the Service User.
Refresh is handled automatically by CaaS during API calls. The Client does not notice any refresh (apart from a longer latency during refresh). However, refresh is only attempted if the Service User invokes an API call for a given End-User.
On Service Provider side the refresh is completely identical to the one without CaaS.
CaaS will only stop trying to refresh a specific token once the Service Provider response contains the error code invalid_grant. Any other error (e.g., internal server error) will result in retry attempts.
If the service provider has at any point responded with the error code invalid_grant, CaaS will set the corresponding CaaS permission to expired as well. The result is, that the Service User will have to create a new permission and complete a new consent-flow before he can access any data from the respective user again.
Multiple tokens for the same Service Provider
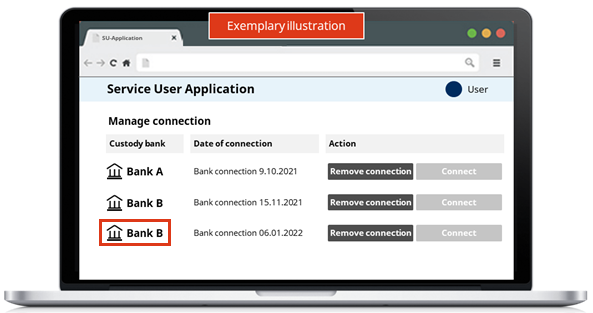
A customer (user) of a Service User may have two or more e-banking accounts (contracts) with the same Service Provider. If the user wants to integrate both e-banking accounts into their Service User application, then the application should ensure the handling of more than one token.
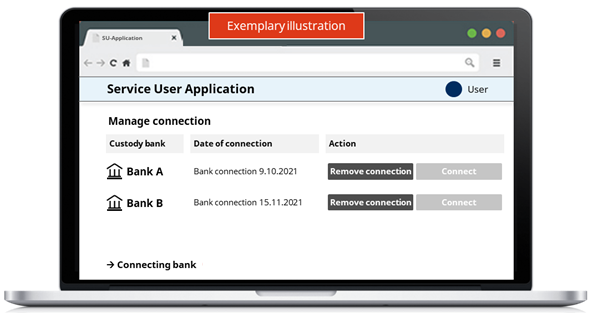
For example, suppose that an employee of an external asset manager (EAM) uses a Portfolio Management System (PMS) application works with Bank A and Bank B. He has already integrated both banks at once by going through the Consent Flow. But the EAM employee also has a second e-banking account with Bank B and he also wants to connect the second account to the PMS application. For this, he has to restart the Consent Flow. The steps of this process are presented as follows:
- First of all, the user has to log into the Service User application, where they get an overview of the banks with which they have already established a connection, as presented in the figure.
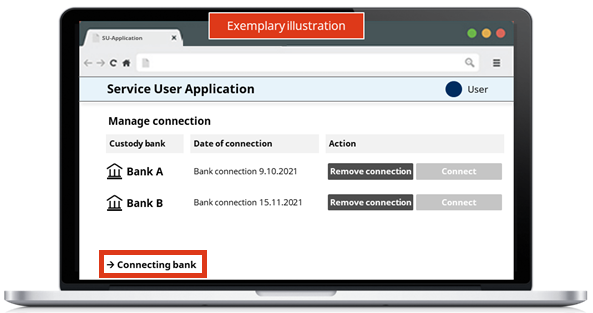
- After that, the user needs to click on "Connecting bank" in order to start a new Consent Flow.
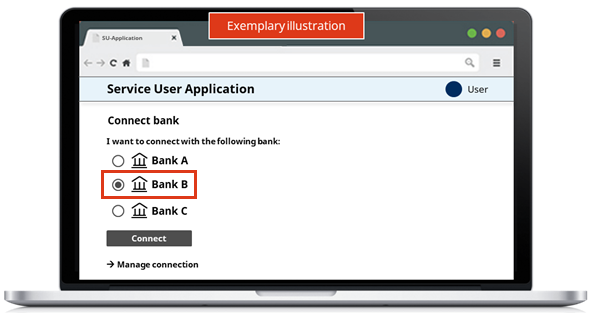
- The user has to select Bank B and click "Connect".
- Finally, after giving the Consent for the second e-banking account of Bank B, the user will be redirected to the connections page. Both connections are now visible in the Service User's application and the user can manage these connections individually.
Existing Consents can't be updated through the bLink APIs. The bLink ecosystem only supports creating new consents because in consent-flow 2.0, there is no parameter which would allow to identify a specific consent. Any changes to existing consents have to be done purely on Service Provider side without any interaction through bLink.