Inter-App Consent Flow
Inter-App Consent Flows are standard OAuth 2.0 consent flows. Using Inter-App URI communication enables OAuth consent flows between any combination of native apps and websites, e.g., App2App, App2Web, Web2App and Web2Web.
The concept is specified in the Best Current Practice OAuth 2.0 for Native Apps (RFC 8252).
This blueprint shows how Inter-App Consent Flows are expected to work with bLink Consent 2.0 and CaaS.
In addition, the blueprint gives technical hints and guidelines for the implementation of native apps.
Conceptual view
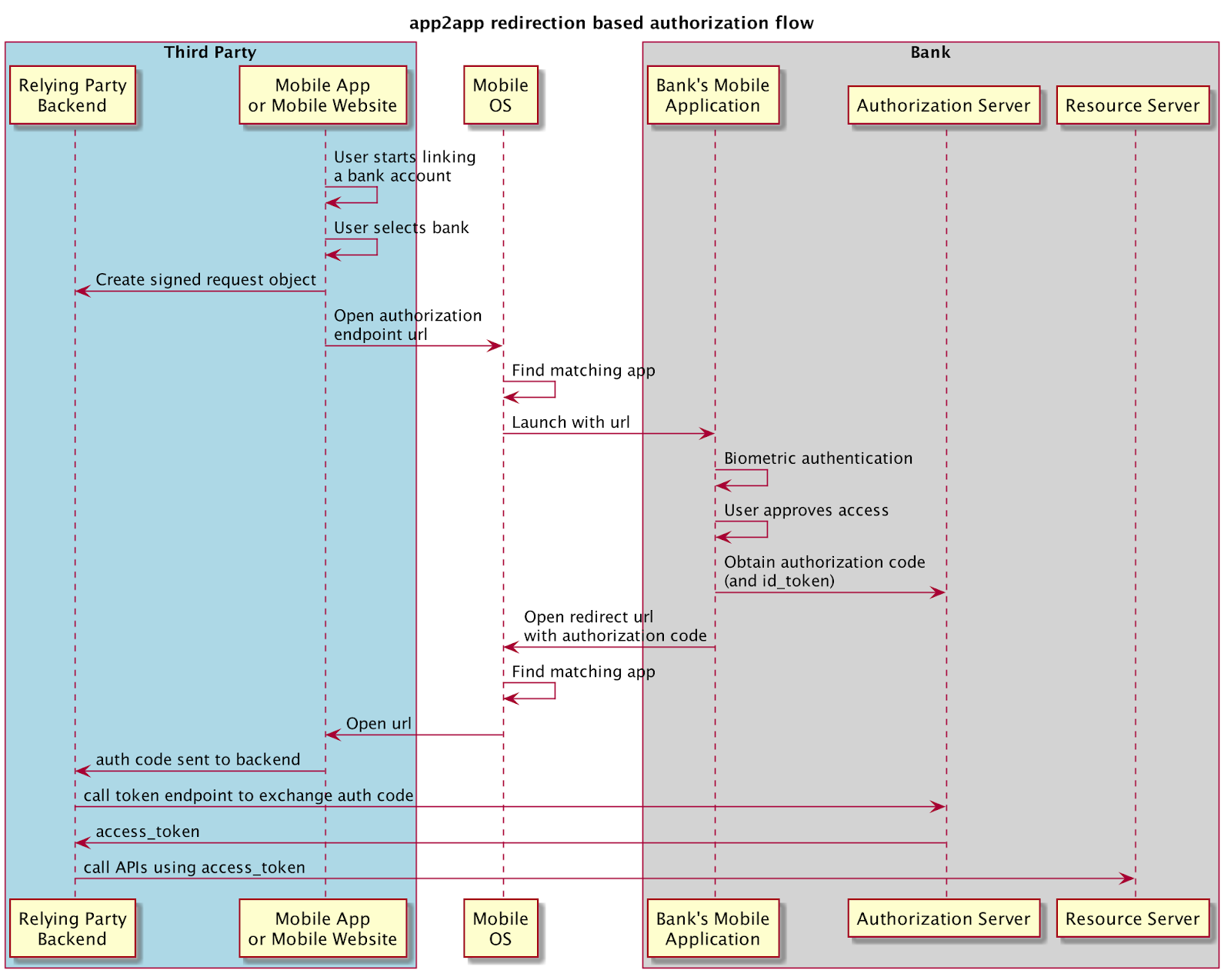 Source: openid.net
Source: openid.net
Inter-App Consent flow in bLink
Overview
This overview focuses on the relevant steps for Inter-App consent flows shown in the red boxes.
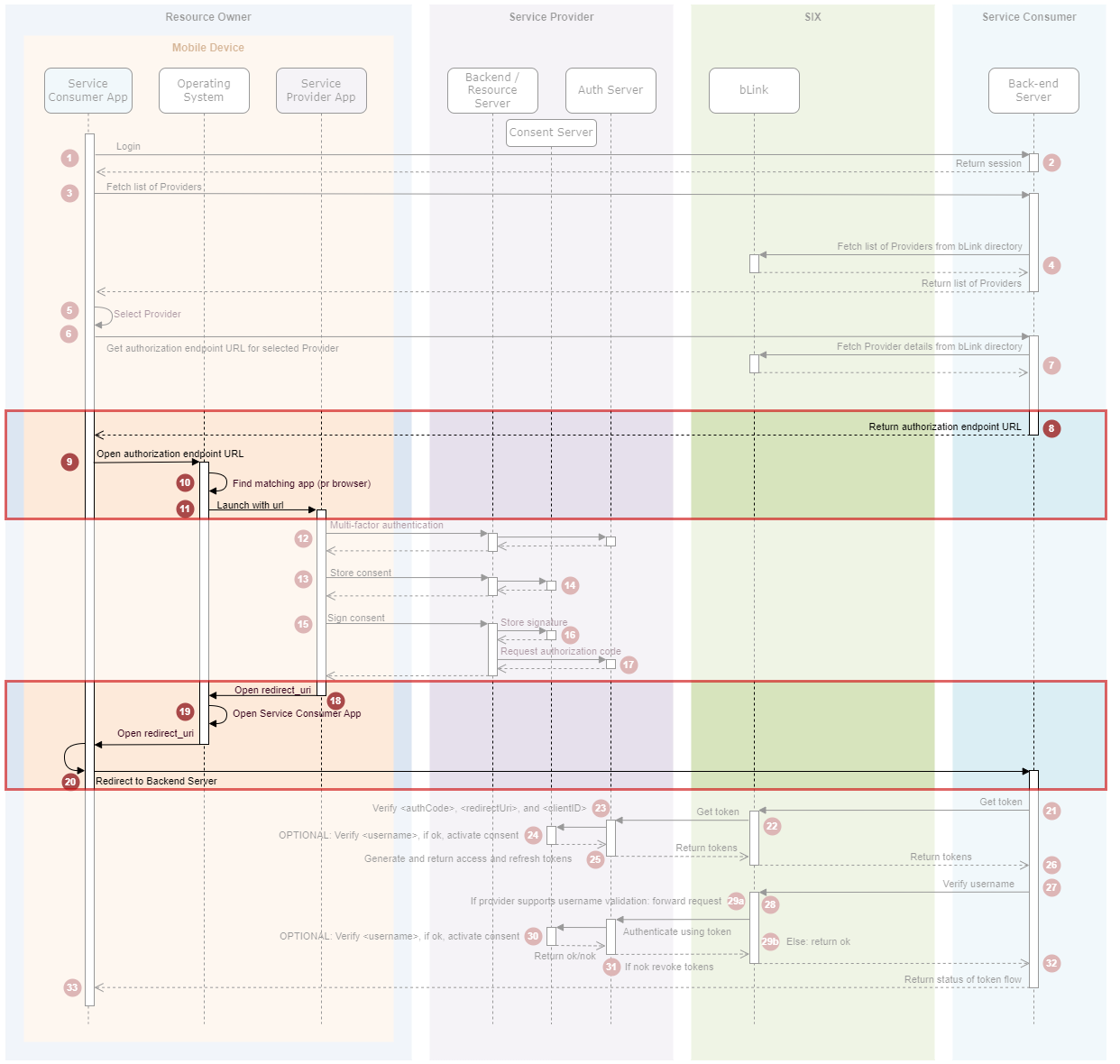
Description of steps relevant for Inter-App Consent Flows (red boxes)
OAuth2 Authorization Code Grant Flow
| Step | Description |
|---|---|
| 8. | Back-end Server creates authorization endpoint URL using a redirect URI capable of being receipt by the Service Consumer App. |
| 9. | App uses platform-specific APIs to open the authorization endpoint URL (further details below). |
| 10. | The Operating system of the mobile device checks whether the authorization endpoint URL is registered by a Service Provider App. |
| 11. | If so, this app is launched with the url. If not, the url is opened in the user-agent (which typically leads to the web application of the Service Provider). |
| ... | User defining and signing the consent |
| 18. | The Service Provider App uses platform-specific APIs to open the redirect URI (further details below). |
| 19. | The Operating system of the mobile device checks whether the redirect URI is registered by a Service Consumer App. |
| 20. | If so, this app is launched with the URI, and the app forwards the authorization code to the Service Consumer to initiate the token request. If there is no app registered for the URI, the URI is opened in the user-agent (which typically leads to the web application of the Service Consumer). |
Inter-App Consent flow in bLink with CaaS
Overview
This overview focuses on the relevant steps for Inter-App consent flows with CaaS shown in the red boxes.
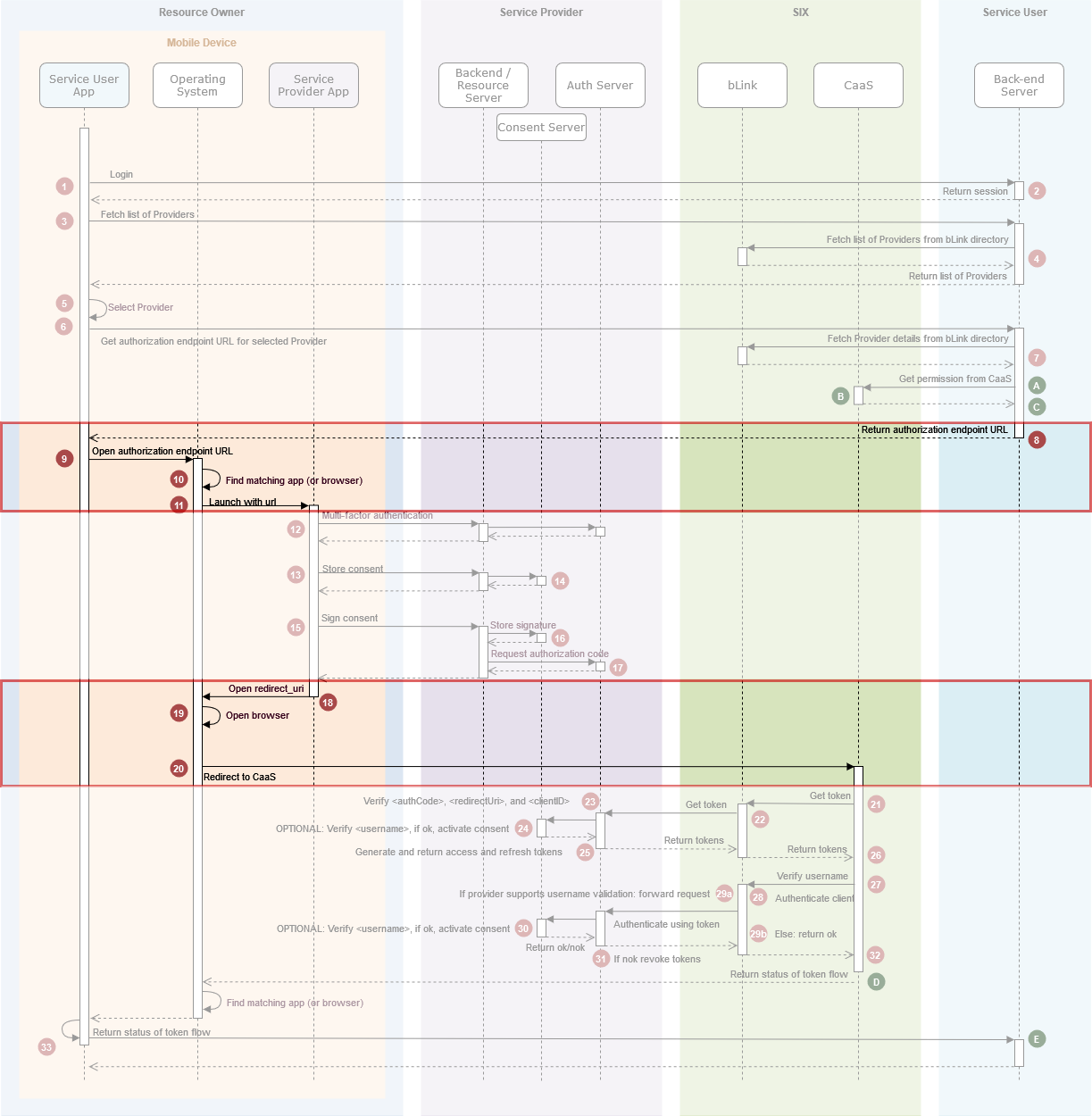
Description of relevant steps for Inter-App Consent Flows with CaaS
Pushed Authorization Request Flow (green bullets)
Flow steps before OAuth2 consent flow
| Step | Description |
|---|---|
| A. | Back-end server posts a permission request to CaaS. |
B. | CaaS creates (or updates) a permission using the clientId, userId, username, providerId, scope and optional externalReference from the request. CaaS generates a redirect URI and a state and adds them to the permission. The permission is stored and returned to the back-end server. |
| C. | Back-end server stores the permission in the context of the user. |
Flow steps after OAuth2 consent flow
| Step | Description |
|---|---|
| D. | CaaS redirects back to back-end server indicating the status of the OAuth2 consent flow (via the Consumer App). |
| E. | Depending on status of OAuth2 consent flow the back-end server uses the externalReference to retrieve the updated permission from CaaS and handle its own state. |
OAuth2 Authorization Code Grant Flow (red boxes)
| Step | Description |
|---|---|
| 8. | Back-end Server creates authorization endpoint URL using a redirect URI capable of being receipt by the Service Consumer App. |
| 9. | App uses platform-specific APIs to open the authorization endpoint URL (further details below). |
| 10. | Operating system of a mobile device checks whether the authorization endpoint URL is registered by a Service Provider App. |
| 11. | If so, this app is launched with the url. If not, the url is opened in the user-agent (which typically leads to the web application of the Service Provider). |
| ... | User defining and signing the consent |
| 18. | The Service Provider App uses platform-specific APIs to open the redirect URI (further details below). |
| 19. | The Operating system of the mobile device checks whether the redirect URI is registered by a Service Consumer App. |
| 20. | In the case of CaaS, there is no app registered for the URI, since it points to CaaS. The URI is opened in the user-agent, and the flow continues with CaaS. |
Pre-requisites
General
The Best Current Practice considers the browser as the recommended user-agent (see technical integration aspects for iOS and Android below)
Service Consumer Application
The Service Consumer App SHALL open the authorization endpoint URL in either an external browser or a custom browser tab (or similar). It is not allowed to use a user-agent that gives full control to the Service Consumer app (e.g., WebViews SHALL NOT be used).
In any case it is required that the URL and the green lock item are shown so that the user can verify the correctness of the destination domain.
The Service Consumer App SHALL register a claimed "https" scheme URI to allow for the resumption of the flow in the app.
Service Provider Application
If the Service Provider provides an application, it SHALL open the redirect URI in the same way as the Service Consumer app opens the authorization endpoint URL (no WebViews allowed).
The Service Provider App SHALL register the authorization endpoint url as a claimed "https" URL to allow initiation of consent flow in the app.
Additionally, the Service Provider SHOULD implement the claimed authorization endpoint URLs in his web-application as well. So to handle the case where no Service Provider app is installed on the device (most likely this url forwards or redirects to the "real" authorization endpoint url or to an informational/support page).
Technical implementation guidelines
Android
Initialize the Service Provider authorization endpoint URL
- in step 9 above
- use a Custom Tab as user-agent
- Custom Tabs in Android «make transitions between native and web content more seamless without having to resort to a WebView»
- Custom Tabs allow users to see the URL that is loaded and to see the SSL verification lock icon to check the correct certificate, basically giving users confidence before entering their sensitive credentials (username and password) and allowing them to perform the checks that our security awareness guidelines recommend them.
Example authorization endpoint URL:
https://consent.mybank.com/consent/c/cls/auth?response_type=code&client_id=<YOUR_CLIENTID>&redirect_uri=<YOUR_REDIRECT_URI>&state=<YOUR_STATE>&scope=<YOUR_SCOPE>&username=<YOUR_USER_ID>&provider_id=<YOUR_PROVIDER_ID>
- following Oauth 2.0 for Native Apps: https://www.rfc-editor.org/rfc/rfc8252.txt , Appendix B.2 for Implementation Guidance
- further instructions: https://developer.chrome.com/docs/android/custom-tabs/
Allow Service Provider App to launch automatically during Login
- Service Provider should implement Google App Links to achieve this.
- No further action is required for Service Consumer on Android.
- This is mandatory for the flow to work correctly, e.g., to automatically open the Service Provider App during the Login flow.
Add app in the referrer
Reasoning:- For easy debugging and usage analytics, the Package Name and version shall be written into the referrer.
- Allows Service Provider to distinguish between mobile and desktop devices.
- see https://developer.chrome.com/docs/android/custom-tabs/best-practices/#add-your-app-as-the-referrer
Do not override the default user agent
Reasoning:- The user agent shall not be overridden.
- Service Provider Login and Consent may not work correctly if the default user Agent from «Custom Tabs» is overwritten.
Handle the non-happy flow: User closes the Custom Tab before the redirect from Service Provider to the Service Consumer
- Service Consumer app shall launch the Custom Tab Activity using Activity Result APIs. Eventually the app may use the underlying "s
tartActivityForResult()" and "onActivityResult()" APIs on the Activity class (or any contract that fits the needs).
- When the user clicks on «X» before the process is fully completed, the app will receive a result with a result_code «
RESULT_CANCELED».
Handle the happy flow: Have the redirect_uri handled correctly.
- The redirect_uri set in step 8 above is intercepted by the native app implementation.
- The recommended way is to utilize the claimed "https" scheme URI Redirection, e.g., create a Google App Link.
- see https://www.rfc-editor.org/rfc/rfc8252.txt , Section 7.3
iOS
Initialize the Service Provider authorization endpoint URL
- in step 9 above
- use an ASWebAuthenticationSession or a SFSafariViewController as user-agent
- when using ASWebAuthenticationSession set prefersEphemeralWebBrowserSession = true
- Prevent sharing of user’s cookies or other browser data for enhanced privacy of Service Consumer app users.
Example authorization endpoint URL:
https://consent.mybank.com/consent/c/cls/auth?response_type=code&client_id=<YOUR_CLIENTID> &redirect_uri=<YOUR_REDIRECT_URI>&state=<YOUR_STATE>&scope=<YOUR_SCOPE>&username=<YOUR_USER_ID> &provider_id=<YOUR_PROVIDER_ID>
- following Oauth 2.0 for Native Apps: https://www.rfc-editor.org/rfc/rfc8252.txt , see Appendix B.2 for Implementation Guidance
- SFSafariViewController: https://developer.apple.com/documentation/safariservices/sfauthenticationsession
- ASWebAuthenticationSession: https://developer.apple.com/documentation/authenticationservices/aswebauthenticationsession
- Further information: https://www.oauth.com/oauth2-servers/mobile-and-native-apps/authorization/
Allow Service Provider App to launch automatically during Login
- Service Provider should implement Universal Link to achieve this.
- Should be allowed by default in the context of ASWebAuthenticationSession.
- When a user returns back to the app, the Authentication Session (that loads the Service Provider App) should still be displayed, polling for a successfully authenticated session and later displaying the consent.
- This is mandatory for the flow to work correctly, e.g., to automatically open the Service Provider App during the Login flow.
Add app in the referrer
- Not supported by iOS.
Do not override the default user agent
Reasoning:- The user agent shall not be overridden.
- Service Provider Login and Consent may not work correctly if the default user Agent from «Custom Tabs» is overwritten.
Handle the non-happy flow: User dismisses the View in the app before the redirect from Service Provider to the Service Consumer
- Handle in the callback the error «
canceledlogin»
- Handling canceled login: https://developer.apple.com/documentation/authenticationservices/aswebauthenticationsessionerror/2991134-canceledlogin
Handle the happy flow: Have the redirect_uri handled correctly.
- The redirect_uri set in step 8 above is intercepted by the native app implementation.
- The recommended way is to utilize the claimed "https" scheme URI Redirection, e.g., create a Universal Link.
- Native app picks up by link, reads out the auth_code parameters and later dismisses the ASWebAuthenticationSession manually by calling cancel() on it (see reference)
- Handling ASWebAuthenticationSession cancellation: see https://stackoverflow.com/a/71180650
Further References
- Consent Flow: https://openid.net/2019/10/21/guest-blog-implementing-app-to-app-authorisation-in-oauth2-openid-connect/
- iOS Implementation: https://developer.apple.com/documentation/xcode/supporting-universal-links-in-your-app
- Android Implementation: https://developer.android.com/training/app-links/deep-linking
- Android Deep Linking Examples: https://levelup.gitconnected.com/deep-linking-on-android-302fd4ddc67d
- Windows 10: https://docs.microsoft.com/en-us/archive/msdn-magazine/2015/windows-10-special-issue/app-integration-linking-and-integrating-apps-on-windows-10
- OAuth 2.0 for Native Apps: https://datatracker.ietf.org/doc/html/rfc8252